In this article, we will talk a little bit about ISO 27001 and ISO 27002. You may already know that ISO 17799 is now ISO 27002. So we will first cover the Information Security Management System requirements (27001) and then the Code of Practice (27002).
Introduction
ISO/IEC 2700x is the growing family of Information Security related standards, published and maintained by the International Organization for Standardization (ISO). At the time being, the family is consisting of:
- ISO/IEC 27001 — Information security management systems — Requirements
- ISO/IEC 27002 — Code of practice for information security management
- ISO/IEC 27003 — Information security management system implementation guidance
- ISO/IEC 27004 — Information security management — Measurement
- ISO/IEC 27005 — Information security risk management
- ISO/IEC 27006 — Requirements for bodies providing audit and certification of information security management systems
- ISO/IEC 27011 — Information security management guidelines for telecommunications organizations based on ISO/IEC 27002
- ISO/IEC 27031 — Guidelines for information and communications technology readiness for business continuity
- ISO/IEC 27033-1 — Network security overview and concepts
- ISO/IEC 27035 — Security incident management
- ISO 27799 — Information security management in health using ISO/IEC 27002
The following standards are in preparation:
- ISO/IEC 27007 — Guidelines for information security management systems auditing (focused on the management system)
- ISO/IEC 27008 — Guidance for auditors on ISMS controls (focused on the information security controls)
- ISO/IEC 27013 — Guideline on the integrated implementation of ISO/IEC 20000-1 and ISO/IEC 27001
- ISO/IEC 27014 — Information security governance framework
- ISO/IEC 27015 — Information security management guidelines for the finance and insurance sectors
- ISO/IEC 27032 — Guideline for cybersecurity (essentially, 'being a good neighbor' on the Internet)
- ISO/IEC 27033 — IT network security, a multi-part standard based on ISO/IEC 18028:2006 (part 1 published already)
- ISO/IEC 27034 — Guideline for application security
- ISO/IEC 27036 — Guidelines for security of outsourcing
- ISO/IEC 27037 — Guidelines for identification, collection and/or acquisition and preservation of digital evidence
ISO 27001:2005
- Scope
- Normative references
- Terms and definitions
- Information security management system
- Management responsibility
- Internal ISMS audits
- Management review of the ISMS
- ISMS Improvement
Annex
ISO 27001 has been prepared to provide a model for establishing, implementing, operating, monitoring, reviewing, maintaining and improving an Information Security Management System (ISMS). ISO 27001 is applicable to any organization, regardless of size, type or nature. The way an organization builds an ISMS should be a strategic decision. The ISMS is influenced by an organization’s need, objectives, security requirements and its size and structure.
ISO 27001 adopts a process to build an Information Security Management System. The ISMS is designed to ensure the selection of adequate and proportionate security controls that protect information assets and give confidence to interested parties. Prior it is important to understand the importance of:
- An organization’s information security requirements
- Implementing and operating controls to manage that organization's information security risks
- Monitoring and reviewing the performance and effectiveness of the ISMS
- Continual improvement based on objective measurement
ISO 27001 adopts the "Plan-Do-Check-Act" (PDCA) model.
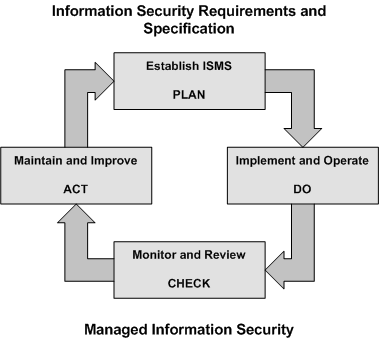
Establishing and managing the ISMS
Establish the ISMS
First step is to establish the ISMS. This is done by defining scope and boundaries of the ISMS, in respect to organization-specific characteristic. The ISMS policy needs to be defined, as well a the risk assessment approach of the organization, which is part of the ISMS policy.
Next steps are all about risk management. The organization must identify, analyze and evaluate the risks. This is done by assessing the business impacts upon the organization that might result from security failures. Upon this, options for the treatment of risks must be considered. Part of this is the selective choice of control objectives and controls. Control objectives and controls must be selected and implemented to meet the requirements identified by the risk assessment and risk treatment process. Keep in mind that activities must be compliant with the amount of risk the organization is willing to take (risk strategy – risk appetite). Once all identified risks have been counter measured, management must approve residual risk.
We know now why, how and what to do, management must now authorize implementation and operating of the ISMS. This also assures resources (time, money, staff …) are available to do so.
An important step is to prepare the Statement of Applicability (SoA). The SoA is a documented statement describing the control objectives and controls that are relevant and applicable to the organization’s ISMS. The controls and objectives are derived from ISO 27002.
Implement and operate the ISMS
The risk treatment plan needs now to be finished with tasks, responsibilities and priorities for managing information security risks. It is one of the most important steps to achieve management commitment for the whole security program. When done, the risk treatment plan with its controls must be implemented in order to achieve control objectives.
An organization should also consider establishing a performance management framework with proper metrics to measure effectiveness of the controls. This allows determining how well controls achieve planned control objectives.
Training and awareness programs and a process for prompt detection of security events and response to security incidents is also required and part of the implement and operating phase.
Monitor and review the ISMS
Implemented controls should be permanently monitored to detect processing errors, as well as attempted and successful security breaches and incidents. This also helps to verify the effectiveness of the security organization. The ISMS must undergo regular reviews to determine effectiveness. This includes policy, controls and objectives, lessons learnt from incidents, feedback and suggestions from interested parties.
Results from risk assessments should be reviewed at regular intervals to comply with the shifting threat landscape. This is to assure the residual risk is still consistent with the risk treatment regulations.
The ISMS should be audited at regular intervals. Update security plans to take into account the findings of monitoring, reviewing and auditing activities.
Maintaining and improving the ISMS
In order to maintain and improve the ISMS, improvements, corrective and preventive actions, derived from the regular updated security plans, must be implemented. Do not forget to take the lessons learnt into account. Ensure that the improvements achieve their indented objects. Communicate improvements to all interested and affected parties.
Documentation requirements
Implementing and establishing an ISMS requires some documentation work. The ISMS documentation should include at least:
- Scope of the ISMS
- Statements of the ISMS policy
- Procedures and controls
- Risk assessment methodology
- Risk treatment plan
- Statement of Applicability (SoA)
Documentation should also include management decisions to ensure actions are traceable and results reproducible. This sounds after a lot of documentation work, but keep in mind that size and complexity of the ISMS depends on an organization’s need, size and structure.
Documents required by the ISMS should be protected and controlled. This includes approval, review, update, versioning, distribution and so on. Records must be established and maintained to provide evidence of conformity to requirements and the effective operation of the ISMS.
Management responsibility
Management commitment
Management must give its commitment for the ISMS by establishing a policy, provide sufficient resources to launch and operate the ISMS, establishing roles and responsibilities, decide upon criteria for risk management, ensure that audits are conducted and perform management reviews of the ISMS.
Resource management
The ISMS managers must determine necessary resources to establish and run the ISMS, whereas it is in the obligation of the management to provide them. Resources are needed to establish, implement, operate, monitor, review, maintain and improve an ISMS and to ensure that business, legal and regulatory requirements are met. The organization must ensure that all personnel who are assigned responsibilities defined in the ISMS are competent to perform the required tasks. This is done by training and awareness. However, for a security program to be effective, an organization must provide training and awareness services beyond security organization boundaries
Internal ISMS audit
The ISMS must undergo regular audits to determine whether it operates as expected and effectively according to the identified security requirements. The responsibilities and requirements for planning and conducting audits, and for reporting results and maintaining records should be defined in a documented procedure.
Management review of the ISMS
The ISMS is monitored continuously and audited at regular interval to ensure its effectiveness and efficiency. Alongside, management should support these efforts by assessing opportunities to improve and change the ISMS. This also included review of the information security policy and security objectives. Results must be clearly documented and recorded.
To do so management can use results from reviews and audits, feedback from interested parties, indicators from performance management (effectiveness management), lessons learnt and status form preventive and corrective actions.
Output from the management review should include decisions and actions to improve the effectiveness of the ISMS, update risk assessment and treatment plan and finally modification of procedures and controls that effect information security as needed due to the shifting threat and requirements landscape.
ISMS improvement
An organization must continually improve the effectiveness of the ISMS through the use of the information security policy, security objectives, review and audit results, analysis of monitored events, performance management framework, corrective / preventive actions and finally management review.
Annex ISO 27001
Statement of applicability
The control objectives and controls for ISO 27001:2005 are directly derived from and aligned with those listed in ISO 17799:2005. An organization may consider that additional control objectives and controls are necessary. Control objectives and controls shall be selected as part of the ISMS process specified in 4.2.1. Altogether they make the “Statement of Applicability” SOA.
Statement of Applicability
The Statement of Applicability is the documented statement describing the control objectives and controls that are relevant and applicable to the organization’s ISMS. Be aware that control objectives and controls must be based on the results and conclusions of the risk assessment and risk treatment processes, legal or regulatory requirements, contractual obligations and the organization’s business requirements for information security.
The SOA is created as follows:
- Go trough all controls (133 as of version 2005)
- Decide whether applicable or not
- Justify why so
- Search for procedure / measure
- Reference procedure / measure in the SOA or describe it
- Document status of each control
You can use the following approach to document the status of each control:
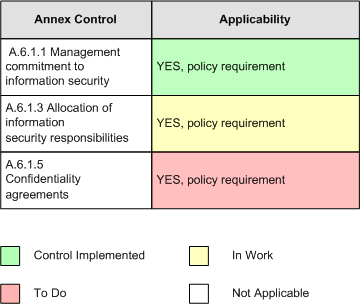
Trough the use of colors the status of measures is now easily visible.
Example of an ISMS TOC
INTRODUCTION
- Objective
- Contents
- Approval and Distribution Policy
ISMS SCOPE
ISMS POLICY
- Risk Management
- Assets
- Business Objectives
- Risk Evaluation Criteria
- Management
- Personnel Policies
- IT
- Forensic
- Documentation
- Other applicable policies
- Certification
INFORMATION SECURITY CONTEXT
- Architecture
- Security perimeter
- Assets
- Threat agents
- Summary of adverse impact
RISK ASSESSMENT AND RISK TREATMENT
- Approach
- Risks concerning business
- Risks concerning theft
- Risks concerning acts of god, vandals and terrorist
- Risks concerning regular fraud
- Risks concerning IT failure
- Risks concerning hacking
- Risks concerning denial of service
- Risks concerning disclosure/misuse of classified information
- Risks concerning law
STATEMENT OF APPLICABILITY
Index
- Index
- Security policy
- Information Security Policy
- Organization of information security
- Internal Organization
- External Parties
- Asset management
- Responsibility for Assets
- Information Classification
- Human resources security
- Prior to employment
- During employment
- Termination or change of employment
- Physical and environmental security
- Secure Areas
- Equipment Security
- Communications and operations management
- Operational Procedures and Responsibilities
- Third Party Service Delivery Management
- System Planning and Acceptance
- Protection against Malicious and Mobile Code
- Back-up
- Network Security Management
- Media handling
- Exchange of Information
- Electronic Commerce Services
- Monitoring
- Access control
- Business Requirement for Access Control
- User Access Management
- User Responsibilities
- Network Access Control
- Operating System Access Control
- Application and Information Access Control
- Mobile Computing and Teleworking
- Information systems acquisition, development and maintenance
- Security Requirements of Information Systems
- Correct Processing in Applications
- Cryptographic Controls
- Security of System Files
- Security in Development and Support Processes
- Technical Vulnerability Management
- Information security incident management
- Reporting Information Security Events and Weaknesses
- Management of Information Security Incidents
- Business continuity management
- Information Security Aspects of Business Continuity
- Compliance
- Compliance with Legal Requirements
- Compliance with Security Policies and Standards
- Information Systems Audit Considerations
ISMS METRICS AND INCIDENT HANDLING
- Introduction
Time theory- Fundamental Principle
- Plan-Do-Check-Act
- Incidents and Impacts
- Impact log
INCIDENT HANDLING PROCEDURE
- Incident Identification and Reporting
- Incident Handling and Escalation
- Communicating Results and Tidying Up
MONITORING CONTROLS
- Check Activities
- Other Metrics
TRAINING AND AWARENESS
OTHER PROCEDURE HANDBOOKS AND MANUALS
DOCUMENT CONTROL
- Introduction
- Document control records
- Change control
- Introduction
- The Change Control Process
- Change Control Procedure
- Document review
- Structural Review
- Technical Review
- Presentation Review
BUSINESS CONTINUITY PLAN
- The Management Process
- Impact Analysis
- The Plan
- Testing
CHECK AND ACT
- General activities
- Special activities
- Internal ISMS audit
- Schedule
- Objectives
- Non-conformities
- Internal ISMS Audit Report and Checklist
- Audit Conduct
- Management review
- Schedule
- Objectives
- Management Review Checklist
- Continual improvement
- Corrective Action
- Preventive Action
RECORDS AND DOCUMENT CONTROL
- Control of ISMS records
- Control of documents
- To do list
ISO 27002:2005
Information is an asset that needs to be suitably protected. Information security is achieved by implementing a suitable set of controls, including policies, processes, procedures, organizational structures and software and hardware functions.
An organization needs to establish an ISMS in order to be able to mange the various aspects of information security. Part of that is the identification of security requirements – these are mainly derived from:
- Assessing risks to the organization
- Legal, statutory, regulatory, and contractual requirements
- The set of principles, objectives and business requirements for information processing that an organization has developed to support its operations
Based on the identified security requirements, an organization then selects the security controls to achieve the desired risk level. What’s left is the residual risk, which is the amount of jeopardy an organization is willing to take (risk appetite).
This is where the ISO 27002 comes into play. It contains 11 security control clauses collectively containing a total of 39 main security categories with a bunch of objectives, controls and executive actions introducing risk assessment and treatment.
Controls considered being essential to an organization from a legislative point of view, due to the fact that most organization must comply with a couple of laws/regulations:
- data protection and privacy
- protection of organizational records
- intellectual property rights
The eleven clauses (accompanied with the number of main security categories included within each clause) are:
a) Security Policy (1)
b) Organizing Information Security (2)
c) Asset Management (2)
d) Human Resources Security (3)
e) Physical and Environmental Security (2)
f) Communications and Operations Management (10)
g) Access Control (7)
h) Information Systems Acquisition, Development and Maintenance (6)
i) Information Security Incident Management (2)
j) Business Continuity Management (1)
k) Compliance (3)
Each main security category consists of:
- a control objective stating what is to be achieved; and
- one or more controls that can be applied to achieve the control objective
Control descriptions are structured as follows:
- Control - the specific control statement to satisfy the control objective
- Implementation guidance - detailed information to support the implementation of the control and meeting the control objective
- Other information - provides further information that may need to be considered
Basic risk management
Risk assessments should identify, quantify, and prioritize risks against criteria for risk acceptance and objectives relevant to the organization. Risk assessments should also be performed periodically to address changes in the security requirements and in the risk situation. The scope of a risk assessment can be either the whole organization, parts of the organization, an individual information system, specific system components, or services.
Treating security risks
Before considering the treatment of a risk, the organization should decide criteria for determining
whether or not risks can be accepted. For each of the risks identified following the risk assessment a risk treatment decision needs to be made. Possible options for risk treatment include:
- Applying appropriate controls to reduce the risks
- Avoiding risks by not allowing actions that would cause the risks to occur
- Transferring the associated risks to other parties, e.g. insurers or suppliers
- Knowingly and objectively accepting risks
Where it has been decided to implement appropriate controls to reduce risks, controls
should be selected and implemented to meet the requirements identified by a risk assessment. Controls should ensure that risks are reduced to an acceptable level taking into account requirements of local and/or international laws and regulations, organizational objectives, requirements and constraints, and of course costs of controls.
Controls can be selected from this standard ISO 27002 or from any other control set, or new controls can be designed to meet the specific needs of the organization. The “Grundschutz” approach from the Bundesamt für Sicherheit in der Informationstechnik (BSI) is generally considered being effective and efficiency. By applying a standard set of controls a general level of information security can be achieved. Special controls are applied to protection objects with elevated security requirements only, as a result of a extended security analysis.
It should be kept in mind that no set of controls can achieve complete security, and that additional management action should be implemented to monitor, evaluate, and improve the efficiency and effectiveness of security controls to support the organization’s aims.
Clauses and security categories
In the following the 11 clauses and 39 main security categories from the ISO 27002 standard. Keep in mind, these are not the controls, it would be beyond the scope of this article to name them all – please refer to the standard for an overview.
Security policy
Information security policy
Objective: To provide management direction and support for information security in accordance with business requirements and relevant laws and regulations.
Organization of information security
Internal organization
Objective: To manage information security within the organization.
External parties
Objective: To maintain the security of the organization’s information and information processing facilities that are accessed, processed, communicated to, or managed by external parties.
Asset management
Responsibility for assets
Objective: To achieve and maintain appropriate protection of organizational assets.
Information classification
Objective: To ensure that information receives an appropriate level of protection.
Human resources security
Prior to employment
Objective: To ensure that employees, contractors and third party users understand their responsibilities, and are suitable for the roles they are considered for, and to reduce the risk of theft, fraud or misuse of facilities.
During employment
Objective: To ensure that employees, contractors and third party users are aware of information security threats and concerns, their responsibilities and liabilities, and are equipped to support organizational security policy in the course of their normal work, and to reduce the risk of human error.
Termination or change of employment
Objective: To ensure that employees, contractors and third party users exit an organization or change employment in an orderly manner.
Physical and environmental security
Secure areas
Objective: To prevent unauthorized physical access, damage, and interference to the organization’s premises and information.
Equipment security
Objective: To prevent loss, damage, theft or compromise of assets and interruption to the organization’s activities.
Communications and operations management
Operational procedures and responsibilities
Objective: To ensure the correct and secure operation of information processing facilities.
Third party service delivery management
Objective: To implement and maintain the appropriate level of information security and service delivery in line with third party service delivery agreements.
System planning and acceptance
Objective: To minimize the risk of systems failures.
Protection against malicious and mobile code
Objective: To protect the integrity of software and information.
Back-up
Objective: To maintain the integrity and availability of information and information processing facilities.
Network security management
Objective: To ensure the protection of information in networks and the protection of the supporting infrastructure.
Media handling
Objective: To prevent unauthorized disclosure, modification, removal or destruction of assets, and interruption to business activities.
Exchange of information
Objective: To maintain the security of information and software exchanged within an organization and with any external entity.
Electronic commerce services
Objective: To ensure the security of electronic commerce services, and their secure use.
Monitoring
Objective: To detect unauthorized information processing activities.
Access control
Business requirement for access control
Objective: To control access to information.
User access management
Objective: To ensure authorized user access and to prevent unauthorized access to information systems.
User responsibilities
Objective: To prevent unauthorized user access, and compromise or theft of information and information processing facilities.
Network access control
Objective: To prevent unauthorized access to networked services.
Operating system access control
Objective: To prevent unauthorized access to operating systems.
Application and information access control
Objective: To prevent unauthorized access to information held in application systems.
Mobile computing and teleworking
Objective: To ensure information security when using mobile computing and teleworking facilities.
Information systems acquisition, development and maintenance
Security requirements of information systems
Objective: To ensure that security is an integral part of information systems.
Correct processing in applications
Objective: To prevent errors, loss, unauthorized modification or misuse of information in applications.
Cryptographic controls
Objective: To protect the confidentiality, authenticity or integrity of information by cryptographic means.
Security of system files
Objective: To ensure the security of system files.
Security in development and support processes
Objective: To maintain the security of application system software and information.
Technical Vulnerability Management
Objective: To reduce risks resulting from exploitation of published technical vulnerabilities.
Information security incident management
Reporting information security events and weaknesses.
Objective: To ensure information security events and weaknesses associated with information systems are communicated in a manner allowing timely corrective action to be taken.
Management of information security incidents and improvements
Objective: To ensure a consistent and effective approach is applied to the management of information security incidents.
Business continuity management
Information security aspects of business continuity management
Objective: To counteract interruptions to business activities and to protect critical business processes from the effects of major failures of information systems or disasters and to ensure their timely resumption.
Compliance
Compliance with legal requirements
Objective: To avoid breaches of any law, statutory, regulatory or contractual obligations, and of any security requirements.
Compliance with security policies and standards, and technical compliance
Objective: To ensure compliance of systems with organizational security policies and standards.
Information systems audit considerations
Objective: To maximize the effectiveness of and to minimize interference to/from the information systems audit process.