Sudo (substitute user do) allows users to run programs with the security privileges of another user, normally the super user (root). Its application is based on the well known fact that one must not have root rights while doing normal business. Sudo allows administrators to give certain type of users or groups root rights for specific commands. Sudo logs its use via syslog for traceability.
Normally, before a user can execute a command with sudo, the user must supply his password. Once authenticated, and if the /etc/sudoers configuration file permits the user access, then the command is executed. Granted access is limited by time, as sudo issues a ticket, allowing the authenticated user only for a few minutes. This timeout may vary between systems and is configurable. Operating systems like Ubuntu and Mac OS X make heavy use of sudo.
There a several graphical frontends for the ease of use, particularly gksudo and kdesu
The "sudoers" file
The file /etc/sudoers defines the rights of the operators. The original file in Slackware looks like this:
# sudoers file.
# This file MUST be edited with the 'visudo' command as root.
# See the sudoers man page for the details on how to write a sudoers file.
# Host alias specification
# User alias specification
# Cmnd alias specification
# Defaults specification
# User privilege specification
root ALL=(ALL) ALL
# Uncomment to allow people in group wheel to run all commands
# %wheel ALL=(ALL) ALL
# Same thing without a password
# %wheel ALL=(ALL) NOPASSWD: ALL
# Samples
# %users ALL=/sbin/mount /cdrom,/sbin/umount /cdrom
# %users localhost=/sbin/shutdown -h now
As noted at the top of the file, it must be edited vi the command “visudo”. Visudo implements a lock mechanism and checks for syntax errors when exiting.
“Host_alias” specification
“Host_alias” specification contains hosts eligible for specific sudo calls. The specification contains a group of computers identified trough either their name or IP address. Keep in mind that this variable only makes sense when using the same Host_alias specification on several computers.
“User_alias” specification
A “User_alias” consists of several members with the same given rights. Example: Specific users could be grouped under a alias which is then allowed to shutdown the computer:
User_alias SHUTDOWN=user1,user2,user3
The alias name must consist of capital letters, numbers or the underscore “_”, user name are separated with a comma. It is possible to combine several alias definitions of the same specification in a single line, separated with a colon
“Cmnd_alias” specification
If you want to use aliases for specific commands, then you might want to use the “Cmnd_alias” specification. Example: Cmnd_alias DOWN = /sbin/shutdown
Example "sudoers" file
Now, suppose you want user1, user2 and user3 be able to shutdown the computer, your /etc/sudoers should look like this:
# Host alias specification
# User alias specification
User_alias SHUTDOWN=user1,user2,user3
# Cmnd alias specification
Cmnd_alias DOWN = /sbin/shutdown
# User privilege specification
root ALL=(ALL) ALL
SHUTDOWN ALL=DOWN
User1 can now invoke the shutdown command with “sudo /sbin/shutdown –h now”, if he provides the correct login password when asked to do so. If you want to suppress the password request, use:
SHUTDOWN ALL=NOPASSWD:DOWN
Use this with caution!
Unauthorized application of sudo
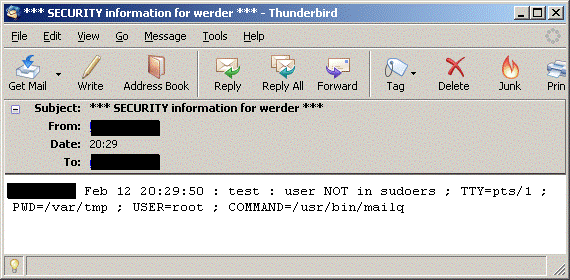
The application of sudo does not weakening the security architecture, if implemented with caution. Nevertheless, every attempt of a unauthorized user to invoke a command with sudo generates a alert message which is sent by email to the super user (root).
Example: User “test” tries to shutdown the computer with “sudo /sbin/shutdown”
User “test” gets the following immediate message: test is not in the sudoers file. This incident will be reported.
User root gets the following email due to the unauthorized application:
Command Parameters
- sudo - K = the sure kill option is like -k except that it removes the user's timestamp entirely. Like -k, this option does not require a password.
- sudo - k = the kill option to sudo invalidates the user's timestamp by setting the time on it to the epoch.
- sudo - l = the list option will list out the allowed (and forbidden) commands for the user on the current host.
- sudo - u = the user option causes sudo to run the specified command as a user other than root. To specify a uid instead of a username, use #uid.
- sudo – v = if given the validate option, sudo will update the user's timestamp, prompting for the user's password if necessary. This extends the sudo timeout for another 5 minutes (or whatever the timeout is set to in sudoers) but does not run a command.
Timeout specification for the granting ticket
The following option in /etc/sudoers defines the timeout for the granting ticket (here: 15m):
Defaults timestamp_timeout=15
sudo in conjunction with the alias command
Sudo is even more powerful in combination with the “alias” command. In the example above, user1 has to type in: “sudo /sbin/shutdown -h now” to shutdown the computer. This can be simplified by defining an alias. This can be a global one in /etc/profile or in the users ~/.bashrc
alias s_off=”sudo /sbin/shutdown –h now”
According to /etc/sudoers user1 is permitted to use the shutdown command. By using the just defined alias he can do this now very simple by typing “s_off”.
My /etc/sudoers consists of a variety of commands, e.g. allowing my personal account to mount / umount shares or even reboot / shutdown the computer. The command below in /etc/sudoers is used by BackupPC – BackupPC is covered by a separate article.
# Settings for BackupPC
amanda ALL = NOPASSWD: /bin/tar